In our highly digital world, investigations contain more digital material every day. From mobile phones and laptops to the cloud and the dark web. Finding and handling these digital materials needs to be done carefully. It is easily compromised, and leads can be hard to find. In any type of investigation, but especially in CSAM investigation. This is where digital forensic investigation makes the difference.
The digital forensic investigation process
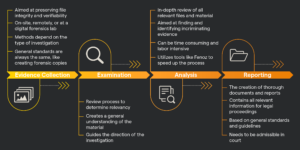
Digital forensic investigation is concerned with identifying, preserving, analyzing, and presenting all forms of digital evidence. Any evidence presented in a legal case needs to be verified. A specific process is used in digital forensic investigations to make sure the digital evidence is handled properly. This process consists of four steps. Collection, examination, analysis, and reporting.
Evidence collection
Evidence can be collected either on-site, remotely, or at a lab. The methods of collection differ per type of investigation, but general standards are always the same. This ensures that the data isn’t lost or changed in the process. A good example is forensic copying. Forensic copies contain all the data of the original material while leaving the original exactly as it is. This way the forensic copies can be further investigated without the risk of altering the original.
Examination
After evidence collection, all material is reviewed to see if it is relevant. This review is not as in-depth as the analysis but is more focused on getting a general understanding of what material is present, and where. Investigators map the digital evidence, how it is organized, and what should or should not be analyzed further. The examination results guide the direction of the digital forensic investigation as a whole.
Analysis
Analyzing digital evidence can be quite an extensive process. Depending on the type of investigation, there can be thousands or even millions of files that need to be reviewed. For this reason, specialized tools exist to help investigators filter through information. A good example is Fenoz, software developed by ZiuZ Forensic Investigation that allows investigators to filter through visual data, such as images or videos. By using Fenoz, an infinite amount of visual data can be examined quickly and efficiently.
Reporting
After investigators have analyzed all the relevant material and identified key evidence, a thorough report needs to be made. These reports are used in legal proceedings. The structure of a report can change based on the investigation type and the parties involved. However, investigators stick to general standards and guidelines to make sure their work holds up in court.
Types of digital forensic investigation
Digital forensic investigation, simply put, is any investigation that has to do with digital evidence. Because there are so many types of evidence and devices, digital forensic investigation includes several branches. These range from working with physical devices to highly volatile network data.
Computer forensics
The first branch in digital forensic investigation is computer forensics. These investigations deal with physical computers and storage devices. Investigators follow a set protocol to recover as much information as possible while making sure it isn’t compromised. In this process, investigators create forensic copies of all evidence. The original devices need to be preserved to prove their legitimacy. Only properly handled digital evidence can be used in the court of law.
Mobile device forensics
Next is mobile device forensics, which includes smartphones, tablets, and GPS devices. The data on these devices is more volatile and gets damaged easily. Additionally, the way to get information from mobile devices varies based on their type and operating system. As there are hundreds of types of mobile devices, many different techniques and guidelines are needed.
Network forensics
The third branch is network forensics. This is where investigators track the activity on a digital network. Because network data is highly dynamic and disappears easily, it is challenging to work with. Retrieving important data needs to be done as swiftly as possible. Additionally, data needs to be analyzed to find not just the content but their origin as well.
Forensic data analysis
Forensic data analysis is often related to financial crimes. In this type of digital forensic investigation, analysts examine data from applications, databases, and systems to find evidence. Special tools and methods are used to analyze and process large datasets effectively.
Database forensics
Database forensics is closely related to forensic data analysis. This type of investigation focuses on databases and the information contained in them. What is there, where did it come from, how was it edited, and when? Databases are usually very large, and are used by several users at once, which poses its own challenges.
IoT forensics
One of the newer branches of Digital Forensic Investigation is IoT forensics, which works with the Internet of Things. A fridge or thermostat can have important info, but getting it is an arduous process for investigators. Additionally, the way these devices create an interconnected system can be very complex.
Digital forensic investigation and CSAM investigation
Digital forensic investigation is vital in the fight against child sexual abuse material (CSAM). With CSAM often taking the form of digital files like images and videos, investigators use digital forensic tools and technologies to prosecute offenders. And CSAM investigation goes even further. Investigators often work on victim identification and use AI-, hash-, and metadata analysis to save victims. From recognizing faces and finding location data to piecing together online conversations and tracing data sources. Creating a complete picture of what happened needs digital forensic investigation tools such as Fenoz.